As the 2024 US presidential election inches closer, Doppel analysts have observed an increase in suspicious online behaviors targeting leading presidential nominees.
Doppel is on a mission to protect humanity from adaptive, GenAI-fueled social engineering and attacks. We are committed to studying social media and domain registrations for indications of election-related misinformation, disinformation, and malinformation (MDM) and fraud. To that end, we have partnered with Defending Digital Campaigns (DDC), a nonpartisan nonprofit that is dedicated to protecting political campaigns from cyberattacks. DDC has worked with numerous candidates from across the spectrum, including notable campaigns like those of Hillary Clinton and Mitt Romney.
In a pro-bono effort to protect our important election process, we are publishing our findings purely so voters, the cybersecurity community, and institutions can be informed and respond appropriately to protect against dangerous actors that threaten our democracy.
Read our previous post from September 2023 centered around election security and online social media impersonation of early candidates in the 2024 Presidential Election here.
Suspicious Domain Findings
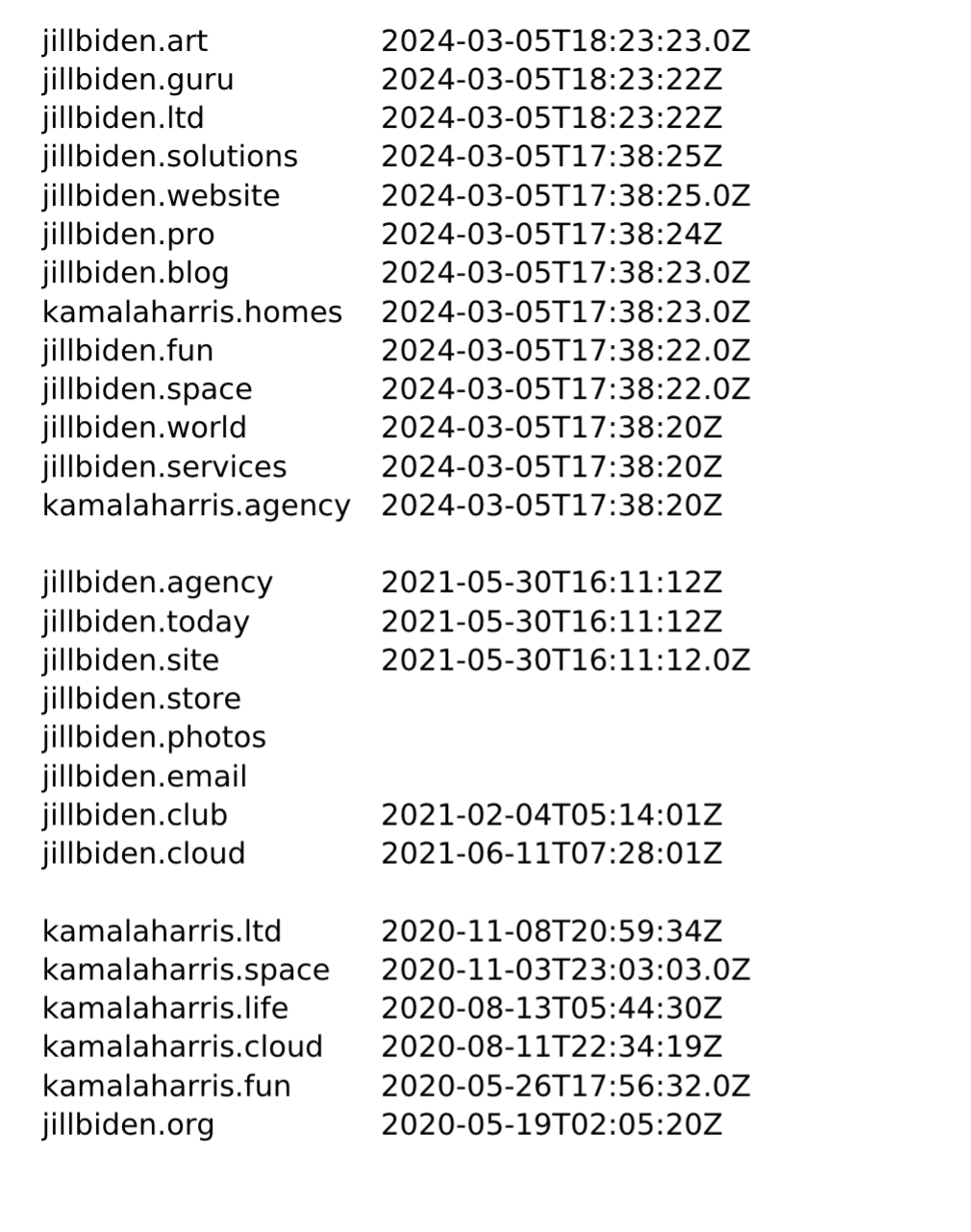
Doppel has detected close to 400 suspicious domains related to major candidates who ran for the 2024 Presidential Election, with almost 200 exclusively linked to Donald Trump, Joe Biden (former candidate at the time of this report), Kamala Harris (current Democratic Nominee), or Robert F. Kennedy Jr. Interestingly, we have observed suspicious behavior from what are likely several unknown actors.
While their intent is unknown, we theorize that these domains, based on behavioral patterns, are being used for malicious purposes. Such purposes include potentially defrauding people through “phishing” schemes, where people are tricked into providing their sensitive and private information. Additionally, impersonators who falsely link candidate campaigns to unsavory behavior can damage a candidate’s reputation.
We have assessed these domains as likely being suspicious due to a combination of factors, including the close proximity in creation dates and the names all being related to Jill Biden or Kamala Harris. This pattern suggests a high likelihood that these domains were registered by a person or persons working in concert.

Further supporting that assessment, we have found evidence that one of these domains has been used in a scam akin to a 419 Nigerian scamming scheme through an email impersonating a state official linked to legitimate Presidential candidate campaigns.
For example, Doppel analysts discovered within our data pool a malicious domain linked to a [email protected], which had recently been called out by 419scam.org for being fraudulent.
Analysis of Defamatory URLs Targeting Candidates
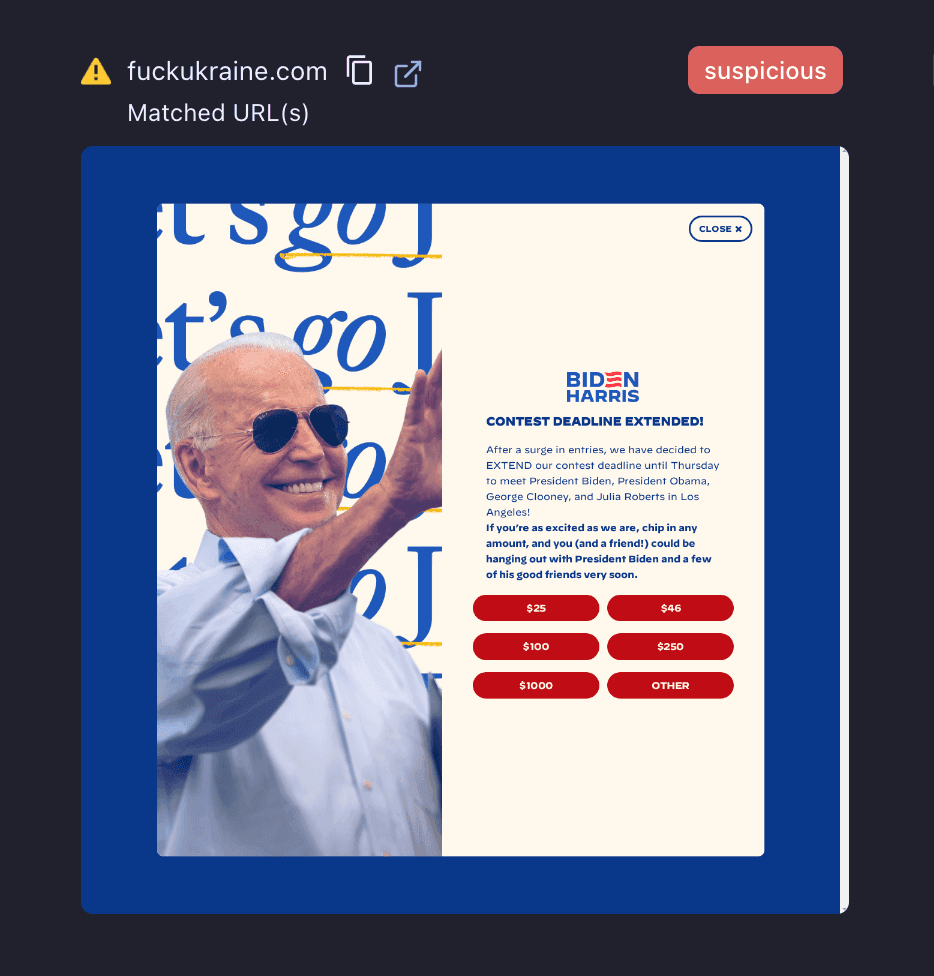
Additionally, Doppel discovered many troll domains such as “pedophile.org” or “fuckukraine.org” that redirect to the official websites for Joe Biden and Donald Trump. Defamatory URLs such as these can act as sources of disinformation as well as link specific candidates or their supporters to false information or ideas with heinous intent.
Social Media Impersonations
Since our last post on candidate impersonators, Doppel has continued its work watching social media impersonations of candidates linked to the 2024 Presidential Election. Doppel has scanned 795 potential fake online personas across social media platforms for the following candidates:
- Joe Biden
- Donald Trump
- Robert F. Kennedy Jr.
Regarding social media, Doppel has observed impersonators typosquatting on official handles, e.g. @RobertKennedyJr on X.
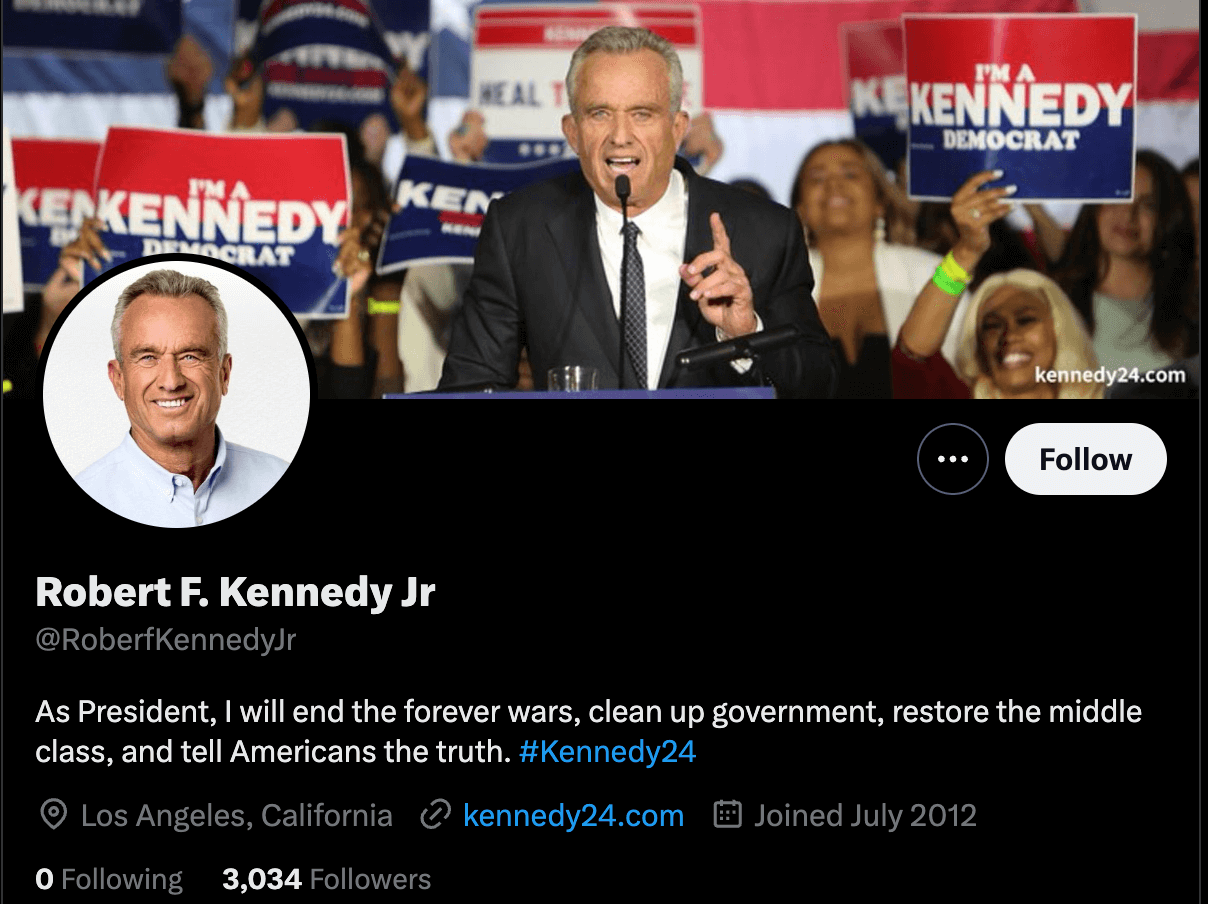
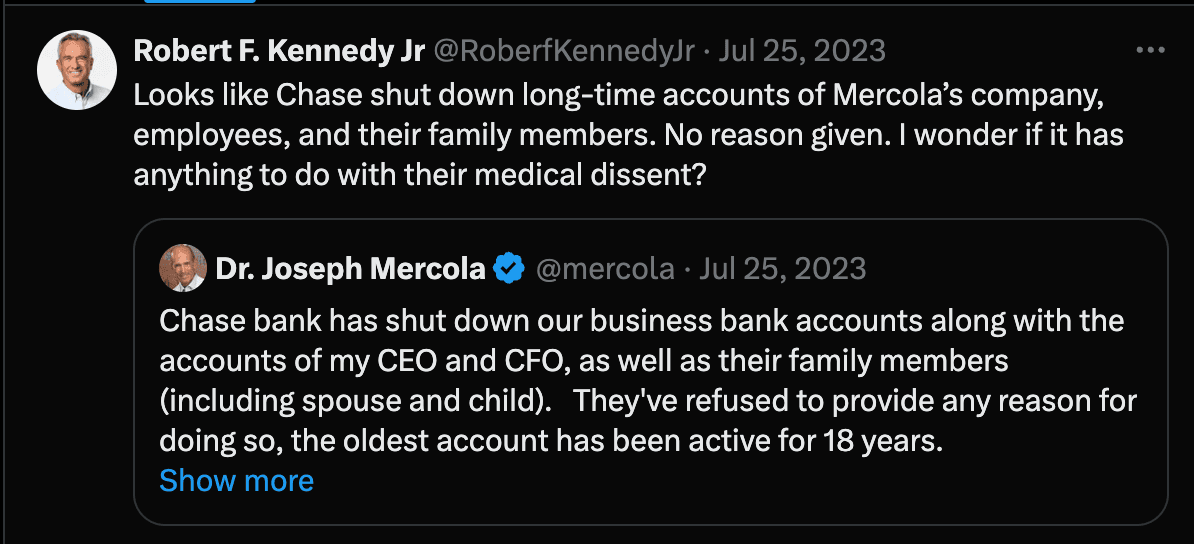
For instance, Doppel analysts identified @RoberfKennedyJr as an impersonation of the official X account of Robert F. Kennedy Jr. (@RobertKennedyJr). While the impersonator does not have a blue checkmark, anyone would be able to purchase a checkmark for $7.99/ month. Many impersonators mimic or plagiarize official tweets and posts as a way to feign legitimacy and divert attention from indicators that they are hosting a fraudulent account.
Fake X Account
Real X Account
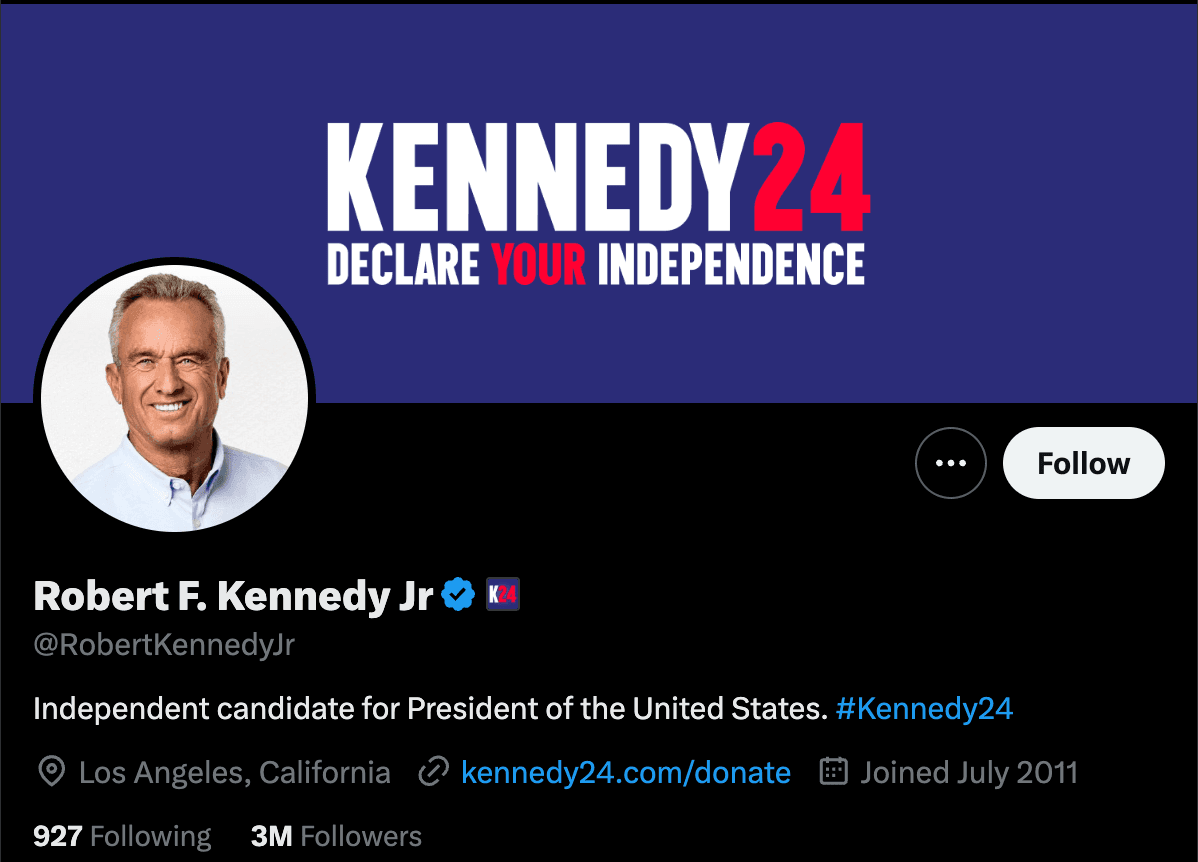
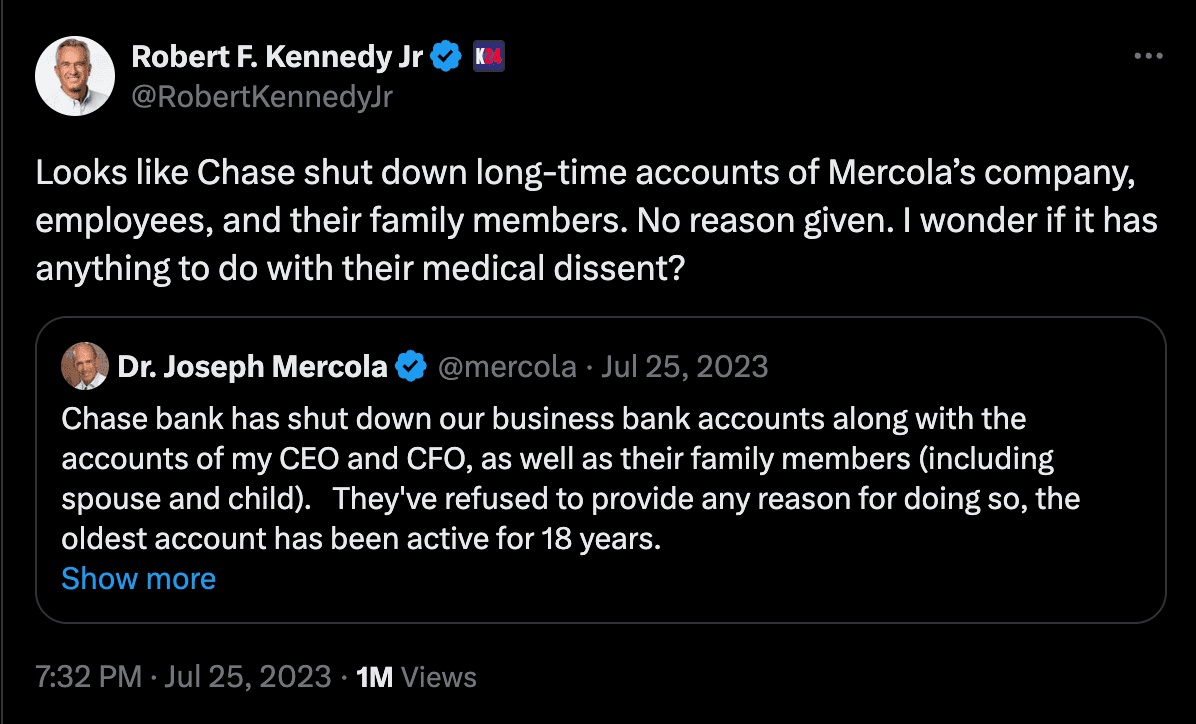
It should be clarified that this impersonating account almost assuredly has not been fraudulently acting as RFK Jr. for 12 years, as indicated by the “joined in 2012” on the fraudulent account’s profile page. Oftentimes criminals hack or purchase aged accounts to better feign credibility. These accounts are valuable assets on the darkweb, as older accounts appear more legitimate to an ordinary user. Furthermore, impersonators can inflate their follower counts by purchasing thousands of bot followers. The purchase of older accounts is a common practice; these accounts are not picked at random but are specifically targeted.
Presidential Candidate Deepfakes
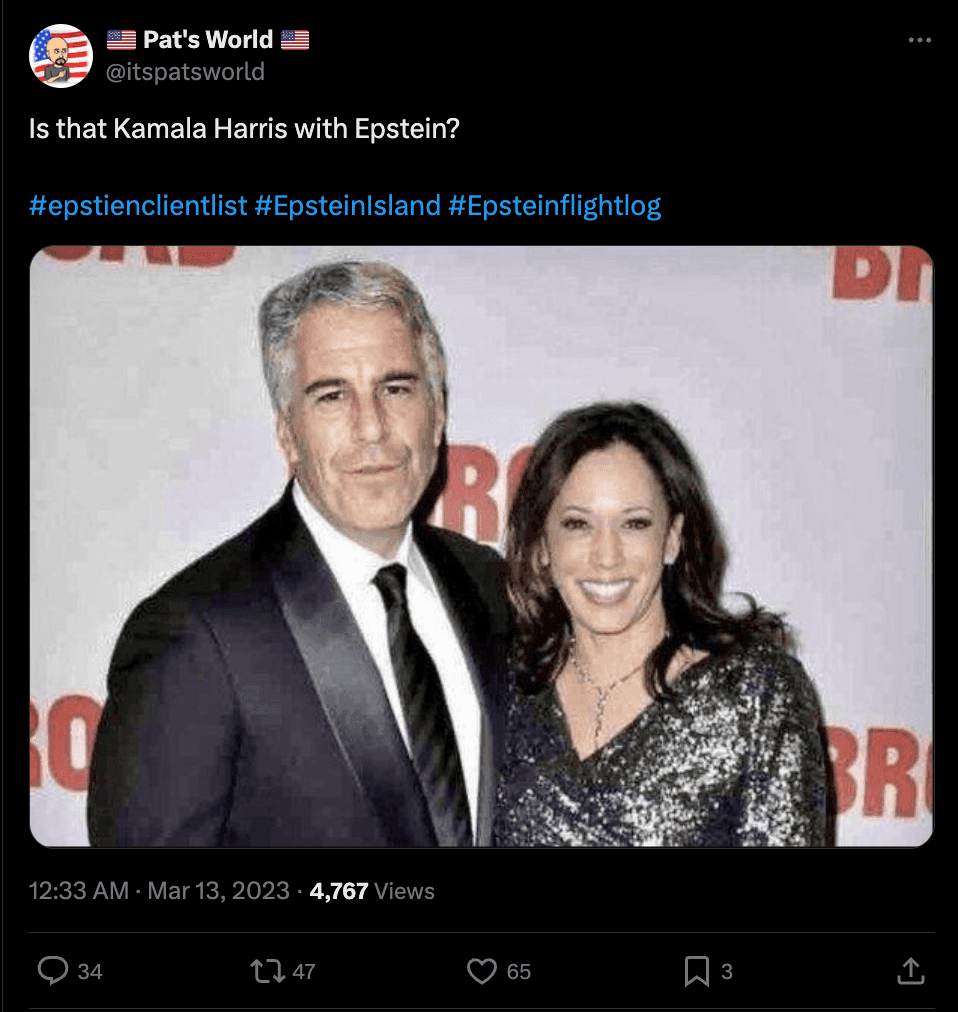
Deepfakes pose significant dangers to federal elections by potentially spreading misinformation and eroding public trust. In the shown example, hours after President Biden stepped down from his re-election campaign, deepfakes focusing on Vice President Kamala Harris began to surface.
These manipulated images and videos can falsely depict candidates making controversial statements or actions, influencing voter perception and decisions. In the deepfaked image below, Kamala Harris’s photo, originally showing her standing with her husband, has been doctored to make it appear as though she is standing closely with Jeffrey Epstein, who was arrested on charges of sex trafficking minors in July 2019.” However, regardless of its falseness the photo has spread throughout social media, garnering thousands of views, ultimately harming the reputation of the Vice President.
The rapid dissemination of deepfakes on social media can outpace fact-checking efforts, leading to widespread false narratives. Such interference can undermine the integrity of the electoral process.
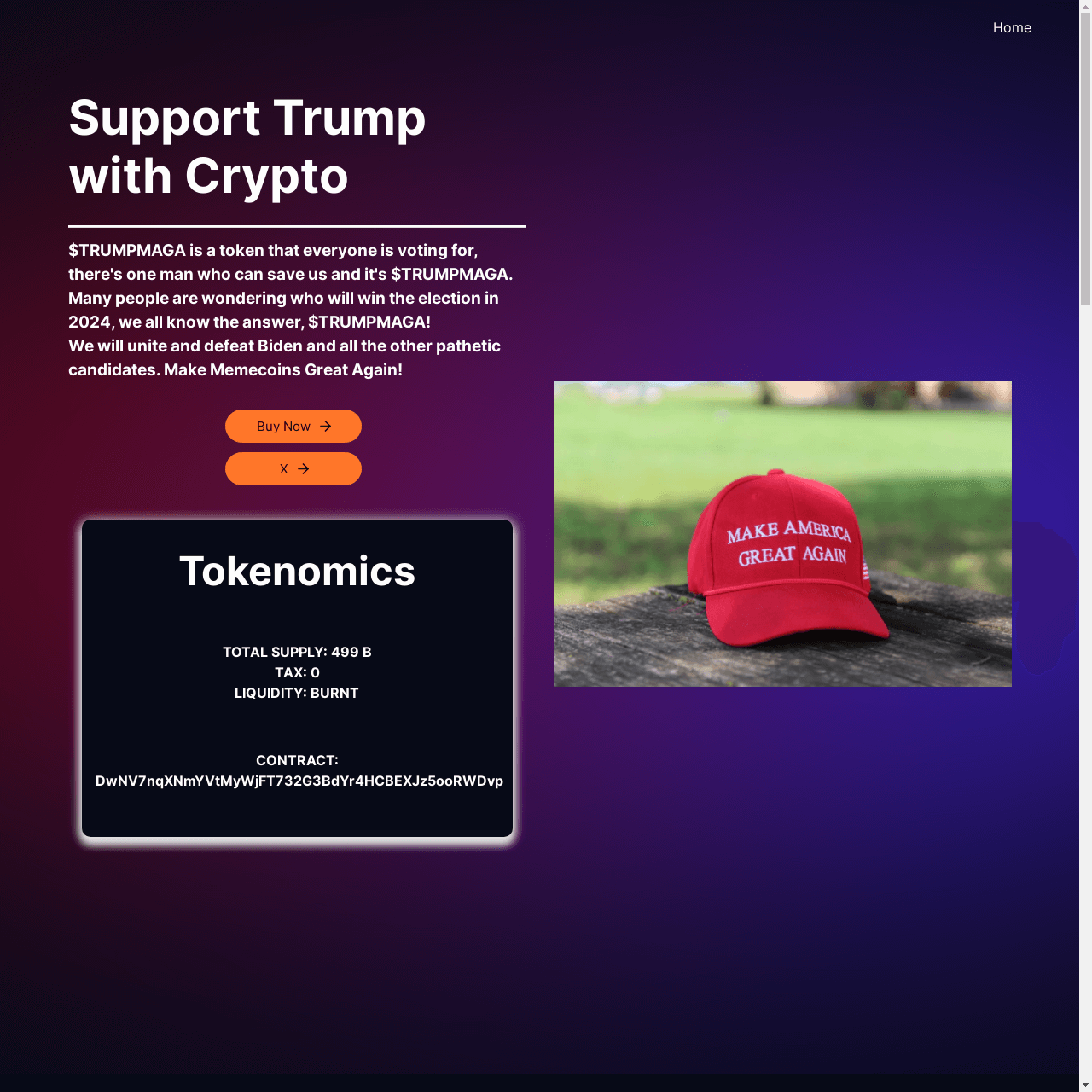
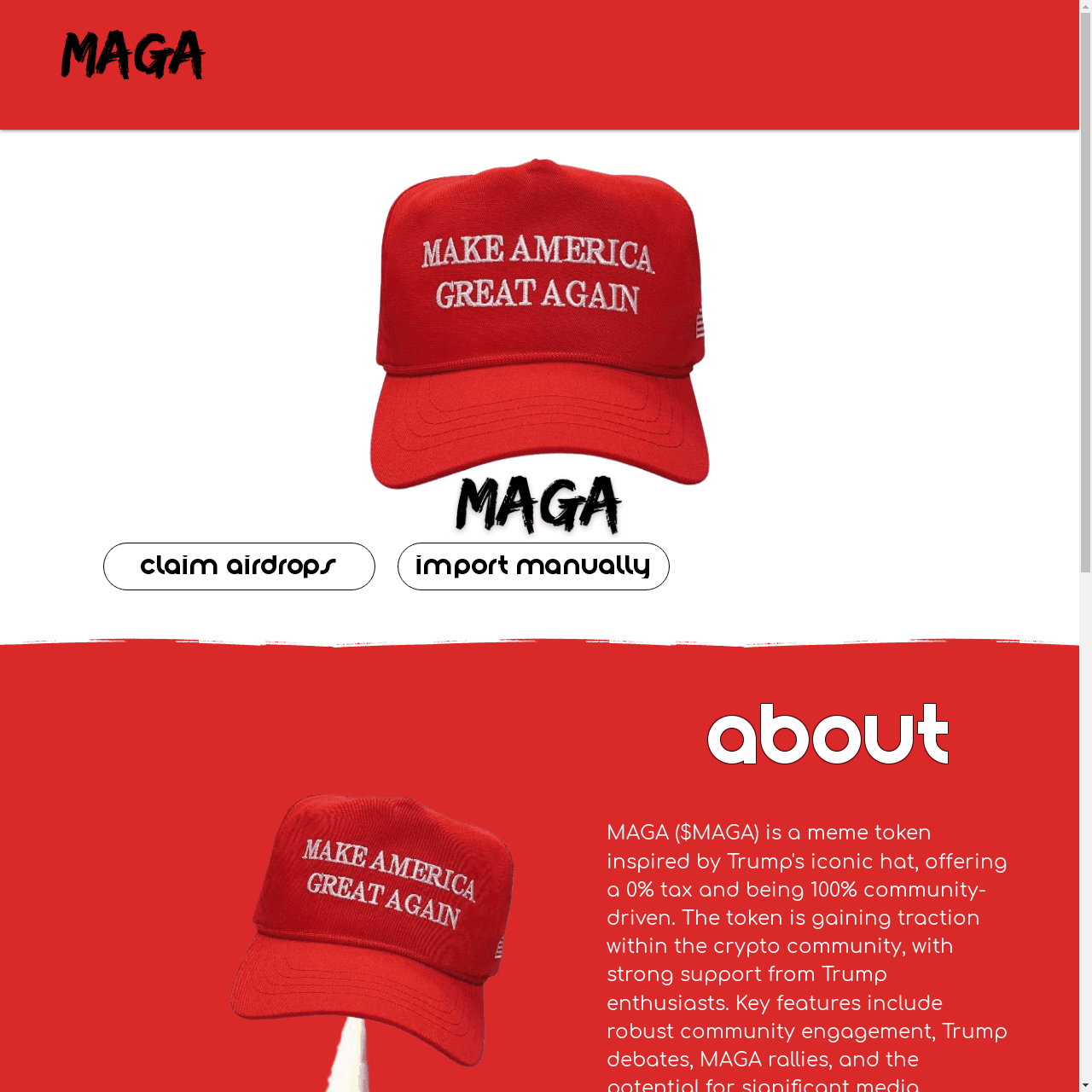
Election-Related Crypto Scams
Another election-related threat Doppel analysts have been monitoring is the growth of so-called “meme coins” that exploit vulnerable people looking to make money through cryptocurrency. Doppel has detected 20+ crypto domains that are centered around presidential candidates. Domains related to these meme coins often ask for sensitive information which can be used for phishing attacks. Since these meme coin domains are not regulated or protected, investors can easily be the targets of additional cybercrimes on these domains.
Coins tied to candidates are driven by misinformation and hype, leading to market manipulation, defamation, and harm to investors. High volatility, speculation, failure to grow investments, or even potential losses can become linked to candidates, subconsciously coloring people’s perspectives of specific campaigns.
Presidential Election Threats in the News
The fear of possible election interference has permeated many legislators’ minds as a legitimate issue that must be handled in the most serious manner. In January, the Associated Press reported that a political consultant by the name of Steven Kramer used an artificially generated message impersonating President Joe Biden in a robocall intended to fraudulently discourage thousands of New Hampshire residents from voting in the Democratic presidential primary.
As part of the scheme, and to increase the likelihood that intended victims would think the call was legitimate, the caller ID spoofed former Democratic State Party Chair Kathy Sullivan’s number. When asked, Sullivan stated the robocalls were “outright election interference, and clearly an attempt to harass me and other New Hampshire voters who are planning to write-in Joe Biden on Tuesday.”
However, the concern over deepfakes is not simply a Democrat fear but is instead quite bipartisan. In June, Donald Trump stated on Jake Paul’s podcast, “Impaulsive”, that he was personally afraid of deepfaked videos potentially triggering a nuclear disaster between nations.
NPR reported that lawmakers in 27 states have already introduced bills to regulate usage of deepfakes in relation to elections. In preparation for the possibility of cybercriminals interfering in elections, the Cybersecurity and Infrastructure Security Agency (CISA) and U.S. Election Assistance Commission (EAC) released a security guide for election officials at all levels of government.
This guide encourages election facilitators to engage in communication with the community, establish official .gov domains, specifically time their messages, and create a fast and straightforward manner for voters to report incidents. Proper reporting and documentation of election procedures both physical and online allow for fast responses and proper protection for everyone involved.
Conclusion
As with any event of national or international importance, elections are a topic criminals consistently use as a theme for fraudulent campaigns. In May, the AP reported that the Federal Bureau of Investigation (FBI) has submitted multiple reports validating the reality of AI being used to spread disinformation in connection to federal elections. Actors and groups aligned with, if not directly connected to, foreign nations continue to attempt to interfere with U.S. elections and negatively impact U.S. national security and confidence in critical pillars of American society (e.g., elections, national health, justice, etc).
Everyone has a part to play in the realm of cybersecurity. No entity has the unilateral power to detect and remove issues seen online. Online communities need to be aware in order to protect themselves. Furthermore, campaigns need to ensure that the proper steps are taken in order to address legitimate cybersecurity concerns.
It is paramount that online users diligently verify links and domains they receive. Here are a few best practices for voters and government officials should follow:
- For government and election security officials:
- Be aware that criminals exploit weak links in communication, especially between government and public
- Monitor online activity for suspicious behavior and ensure proper procedures aren't being interrupted
- Proactively warn the public about specific attacks or rapidly spreading misinformation
- For voters:
- Verify links, domains, and sender addresses before clicking - be wary of phishing attempts
- Use verified information from trusted sources, like .gov websites
- Check URLs and social media handles carefully - criminals may use typos to impersonate legitimate accounts
How Doppel Can Help Protect Political Campaigns
Malicious actors will never stop trying to undermine the United States’ election process, as political campaigns and voters remain common targets of phishing and fraud just as much as large enterprises. Doppel is committed to protecting political candidates at any level and their campaigns from criminals' intent on causing damage and creating mischief for their own profit.
Doppel is collaborating with Defending Digital Campaigns in order to help protect political candidates in the upcoming elections. Both DDC and Doppel are non-partisan, and the process is completely opt-in. We will provide cybersecurity protection for DDC eligible campaigns. This report represents a small fraction of the services that we offer to campaigns who are registered as our official clients. We offer our services in a time when cyber threats and misinformation are pervasive and widespread on social media.
Doppel is providing services pro-bono to all election campaigns, and any political campaign seeking more information can visit: https://www.doppel.com/defending-digital-campaigns


