Security leaders need to keep social engineering attacks and prevention strategies at the forefront of their security efforts to protect both the business and individual team members from significant risks.
Understanding social engineering attacks and their manipulative tactics empowers organizations to respond with clear, actionable insights on how to prevent and respond to threats, safeguarding their organization’s data, systems, and reputation.
To support these efforts, we’ve compiled research on the top 10 types of social engineering attacks to watch for in 2025 with forward-thinking defense strategies that lead to long-term success in combating these evolving threats.
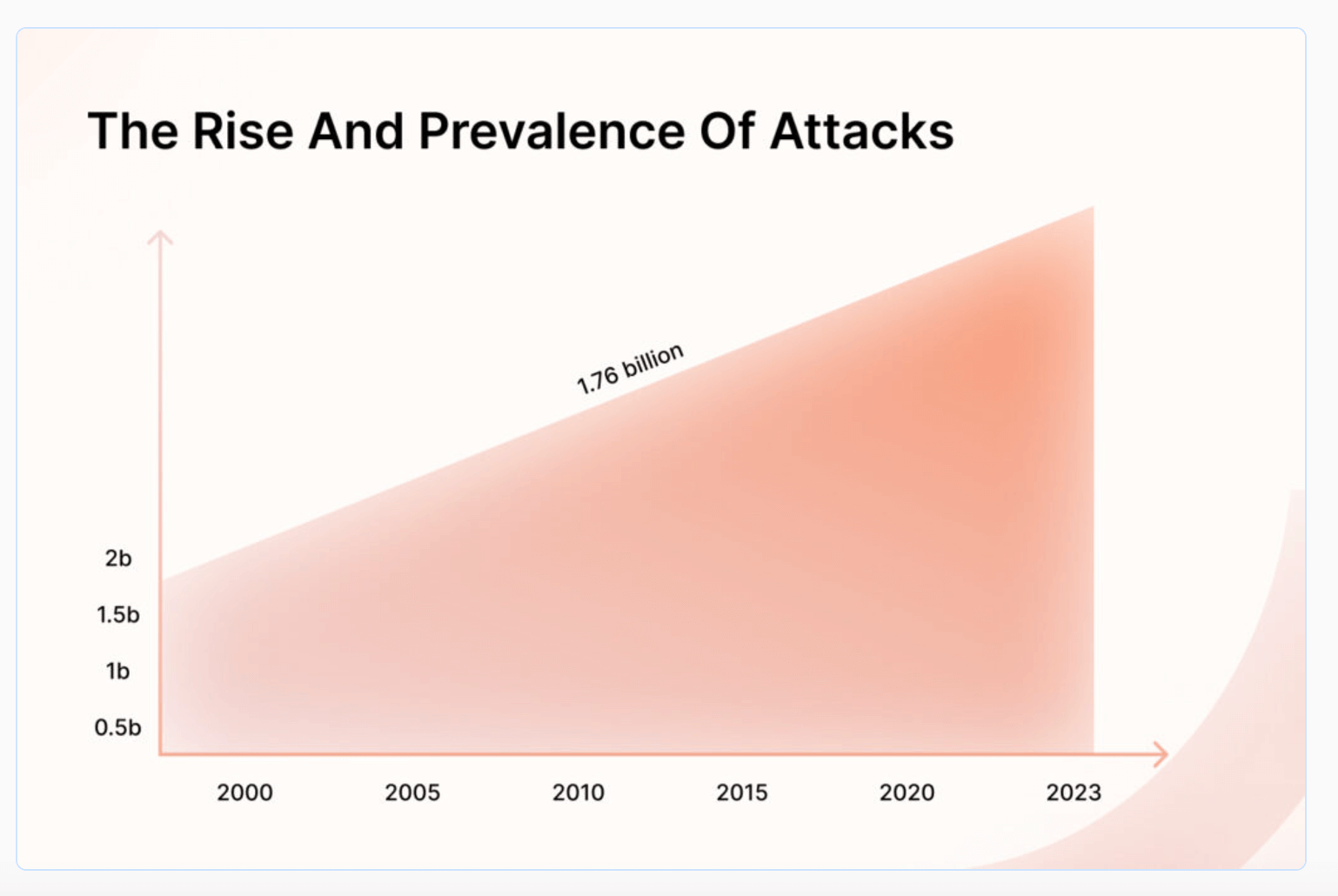
The Rising Threat of Social Engineering to Business Security
Every 11 seconds, there is a successful ransomware attack, according to Enterprise Apps Today. Not only that, but 98% of these attacks were orchestrated from social engineering, and 50% of American organizations are not prepared for these types of attacks, which could end up costing them an average of $4 million — along with lost, irreplaceable data and reputational damages.
To top it off, Sprinto states that nearly 80% of recent social engineering attacks are successful. Social engineering attacks continue to rapidly grow as Google reports a 350% increase in phishing websites since the pandemic in 2020.
10 Types of Social Engineering Attacks Targeting Organizations in 2025
Let’s explore the 10 most critical types of social engineering attacks to watch for in 2025 — with details on how each attack works and common channels used.
1. Phishing
Phishing attacks typically involve fraudulent communications, like emails, to entice the recipient to share sensitive information, such as financial data or credentials, or click malicious links. These messages are often depicted as urgent or intriguing and seem to be sent by legitimate senders, such as a CEO or trusted company, with similar email addresses or messaging that appear normal at first glance. Common channels for phishing include emails, fake websites, and social media platforms.
2. Spear Phishing
Spear phishing is a targeted phishing attack where threat actors tailor their messages to specific individuals or organizations based on researched information. Similarly, attackers may impersonate trusted contacts, such as colleagues or business partners, to extract information or fraud attempts through a personalized message. Attackers frequently exploit email but may also use direct messages on social media like LinkedIn.
3. Vishing (Voice Phishing)
Vishing uses phone calls or voicemail to trick individuals, such as impersonating their banks, tech support, or government agencies. Common tactics include claiming suspicious activity on an account or immediate action is required to avoid penalties. Phone calls, robocalls, and voicemail messages are the main channels for vishing attacks.
4. Smishing (SMS Phishing)
Smishing involves text or SMS messages with probing questions or malicious links to entice the recipient to gain information or inject malware. Typical smishing tactics include deceitful alerts about account issues, package delivery updates, or prizes. Malicious actors primarily use SMS but may also use popular messaging apps like WhatsApp or iMessage.
5. Pretexting
Pretexting is a social engineering technique where a cyberattacker creates a character and backstory, such as an IT admin, HR, or trusted vendor, to manipulate people into divulging information or granting originally undenied access. Common practices include phone calls, emails, or in-person requests for account verification, personal details, or privileged access.
6. Baiting
Baiting lures threat actors' targets with enticing offers, giveaways, or discounted items to manipulate the victims into sharing their personal information or injecting malware into their systems. Common tactics include fake software updates or free trips and prizes through emails, websites, advertisements, or direct mail. Additionally, attackers can use infected USB drives or public QR codes to bait victims.
7. Quizzes and Surveys
Quizzes and surveys are commonly disguised to extract personal information. These quizzes are seemingly fun entertainment but cyberattackers can easily use this tactic to collect birth dates, addresses, or security-related answers. These quizzes and surveys are usually found on social media platforms, websites, or emails.
8. Impersonation
Similarly to pretexting, impersonation involves phishers pretending to be a colleague, vendor, or leader to gain their target’s trust. This tactic is generally used in person, over the phone, or through email, where the attacker uses fake credentials or detailed knowledge about the organization to gain additional access.
9. Business Email Compromise (BEC)
Business Email Compromise (BEC) attacks target organizations by compromising or spoofing legitimate email accounts, such as using amazon.co vs. amazon.com. These subtleties may be difficult to catch, especially when users are working quickly. Attackers can combine this method with pretexting or impersonation to act as a CEO/CISO to request urgent information. The sent emails often appear legitimate and can be followed up with text or phone calls to further verify their story and trick victims.
10. Watering Hole Attacks
Watering hole attacks leverage the user’s regularly visited websites, including forums, social media links, and web pages. Like hunters, the attacker uses the person’s favorite “watering holes” so they do not suspect an infected website. Upon clicking on the website, their endpoint or device can become infected and deploy malicious code throughout their network and infrastructure.
What to Do When a Social Engineering Attack Breaches Your Organization
Breaches happen. According to Sprinto, it took organizations approximately 207 days to identify a breach and 70 days to contain it — costing an average of $4.1 million.
Along with preventive measures, businesses should proactively work to identify and stop breaches quickly to reduce potential costly risks.
If your organization experiences a social engineering attack, here’s what you should do next.
1. Containment
Immediately identify compromised systems, accounts, or networks and disconnect them from the broader infrastructure. Then, disable access for breached accounts, secure backup data for recovery efforts, and notify stakeholders to prevent further engagement.
2. Investigation
Next, assess how the breach occurred, where any information may have leaked, and where there are potential damages. Sadly, only 1/2 of organizations report an attack vector, according to Sprinto, which could lead to missed communication logs and a true understanding of the attacker’s attempt. Incident response (IR) teams can identify further vulnerabilities and forensic analysis of all malicious actions.
3. Recovery
To proceed with recovery, the business must patch vulnerabilities via software updates, access control reconfiguration, and additional DNS and email filtering. Ensure data backups are untouched before reconnecting, mandate password resets for all employees and systems, and continually monitor for threats and warnings.
4. Minimize Damages
Although it may seem counterintuitive to reputational damage, organizations must be transparent about a breach and provide any mitigation steps to affected employees, customers, and partners. Work with legal and public relations teams to handle external communications and regulatory requirements effectively, and implement additional safeguards, such as multi-factor authentication and employee training. Brand protection solutions can also be leveraged to help protect organizations more efficiently.
5. Restore Security and Prepare for Future Incidents
Review IR protocols and address any gaps for future attacks. Conduct post-mortem analysis, document lessons learned for further prevention, and research long-term solutions like additional tools for digital risk protection.
How to Identify and Respond to Emerging Social Engineering Tactics
Being proactive is important to identify and respond to emerging social engineering tactics. Leveraging threat intelligence solutions and employee training is critical to quickly detecting and responding to cyber threats. For more practical tips that organizations like yours can implement today, read our 10 strategies on how to stop social engineering attacks.
Forward-thinking perspectives on social engineering throughout your organization are key to safeguarding businesses and employees. By leveraging executive protection solutions with the use of AI and automation in security response, organizations have been able to reduce the cost of a breach by up to $173,074, according to Sprinto.
Set up your organization for long-term success in combating these social engineering attacks. Request a demo today with Doppel’s social engineering defense platform to fortify your organization’s data, systems, and reputation.