The Blog
Research
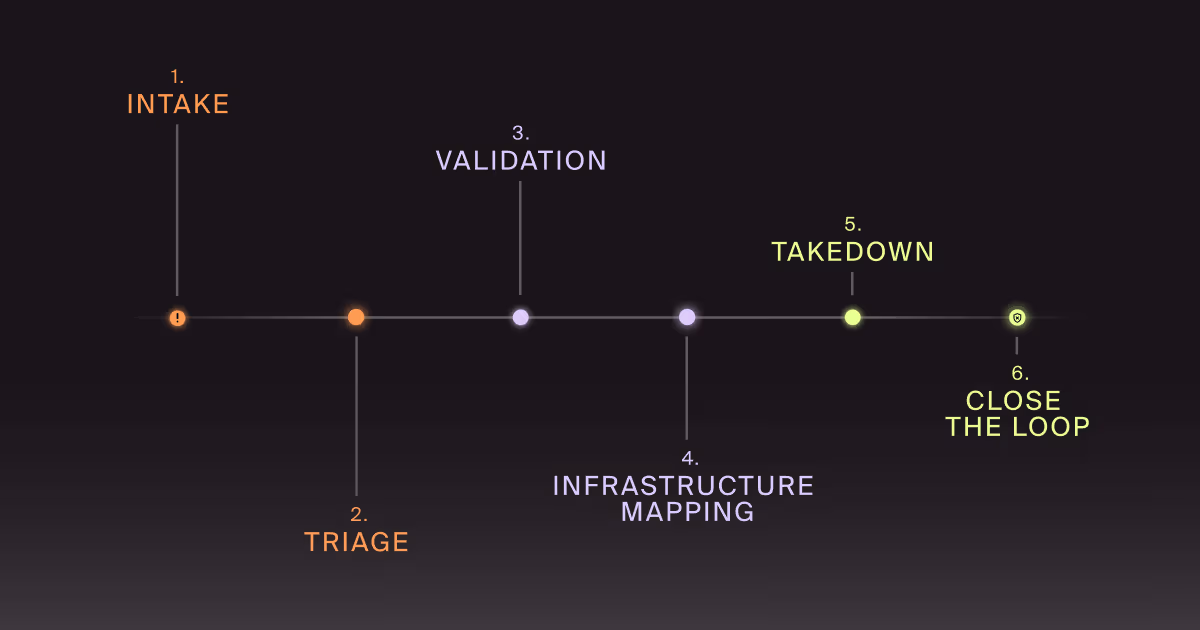
Customer-Targeted Phishing Takedown
A practical workflow to validate, map, and remove phishing infrastructure targeting your customers, plus metrics to prove it works.
Gina Jee
Latest Blog Posts
Research
Recruitment Scams Are Skyrocketing: Here’s Why (& How to Fight Back)
Recruitment fraud is on the rise as scammers use AI to impersonate recruiters from potential employers. Learn the red flags, verification steps, and how brands can stop the impostors.
Gina Jee
Research
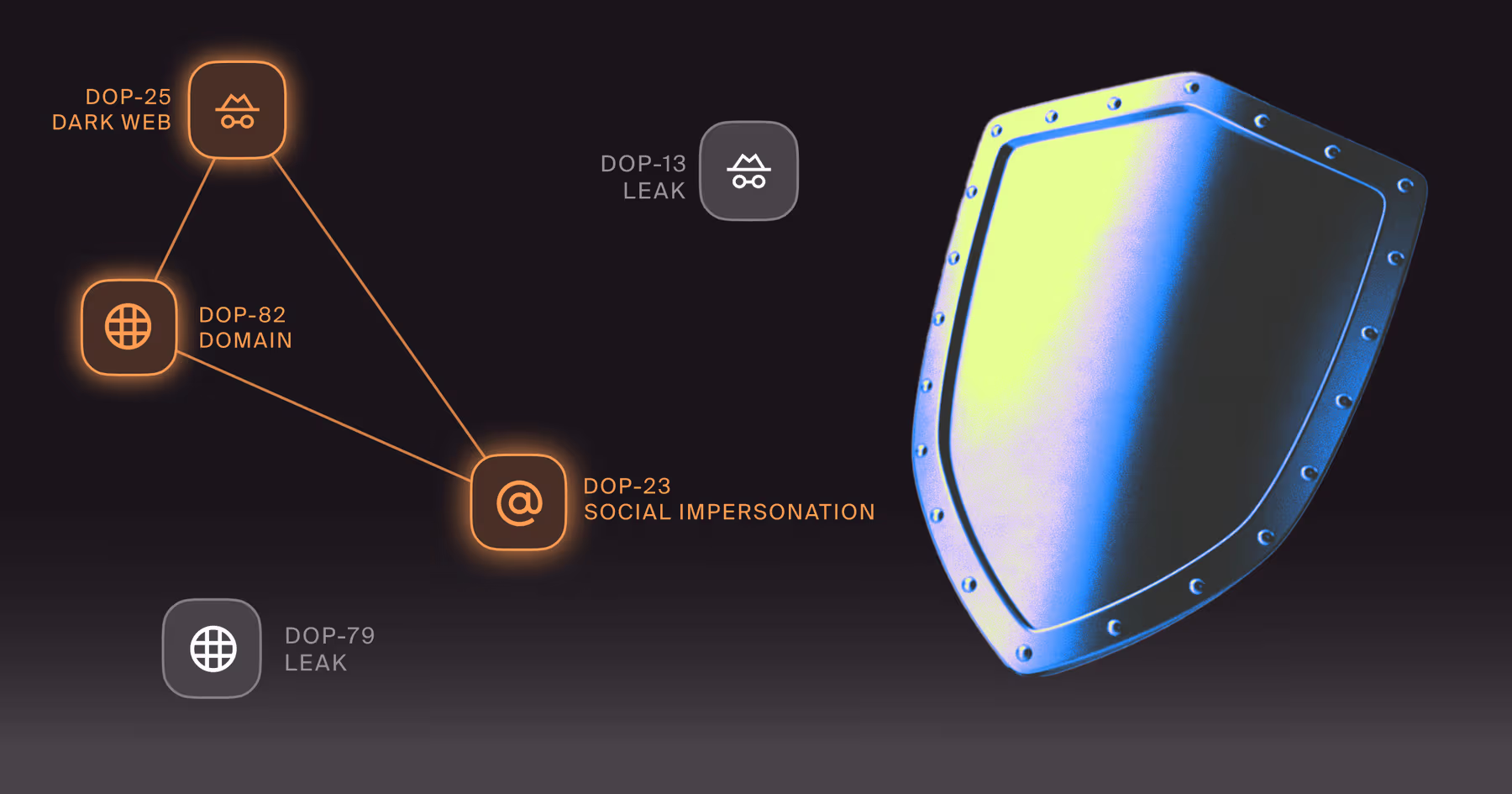
Why Every Brand Needs an Impersonation Attack Response Plan
A practical impersonation attack response plan. Triage, validate, contain, and eliminate attacker infrastructure fast across channels.
Gina Jee
Engineering
The Billion-URL Diet: Cutting Python Loops From Our Pipeline
How we turned a Python-bound pipeline into a columnar, vectorized system built for scale.


Tirath Patel and William Gill

Blog
Customer-Targeted Phishing Takedown

Blog
Recruitment Scams Are Skyrocketing: Here’s Why (& How to Fight Back)
Blog
Why Every Brand Needs an Impersonation Attack Response Plan
Blog
The Billion-URL Diet: Cutting Python Loops From Our Pipeline
Blog
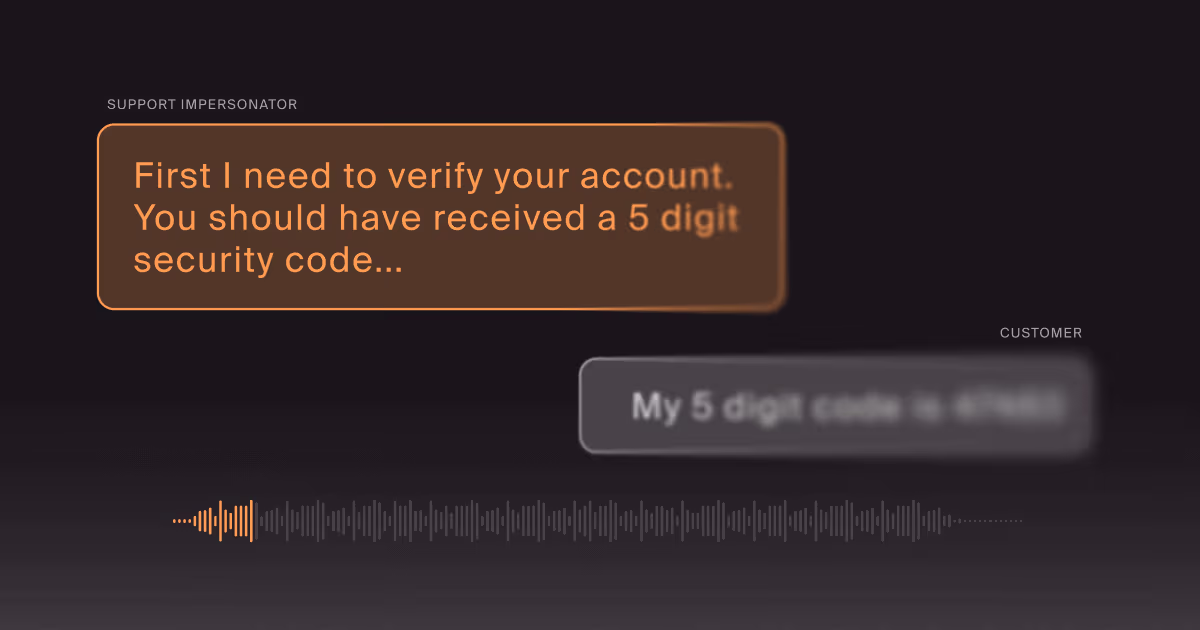
Stopping Vishing Brand Impersonation Before It Reaches Your Customers
Blog
External Phishing Threat Monitoring Explained
Blog
Online Brand Impersonation Reporting for Brands
Blog
Brand Phishing Trends + How to Respond Faster
Blog